The USA trade war with China was started a long time ago. China has been waging economic war against the USA before they joined the World Trade Organization (WTO) in December 2001. Perhaps as early as 1997 when Hong Kong was handed back to China and retaining special financial status to facilitate trade.
The main complaints the USA has against China has to do with unfair intellectual property acquisition and state subsidies to help Chinese companies capture market share. Here is a list of the areas of concern.
- Cyber espionage to steal trade secrets, military secrets, and personal data
- Forced Technology Transfer
- Counterfeited products
- Currency Manipulation
- State owned and/or subsidized companies
- Product dumping below cost to gain market share
Cyber espionage has many faces from malware to direct brute force attacks on exposed servers. A device can be placed within your network with back doors which can be randomly opened to scoop up information.
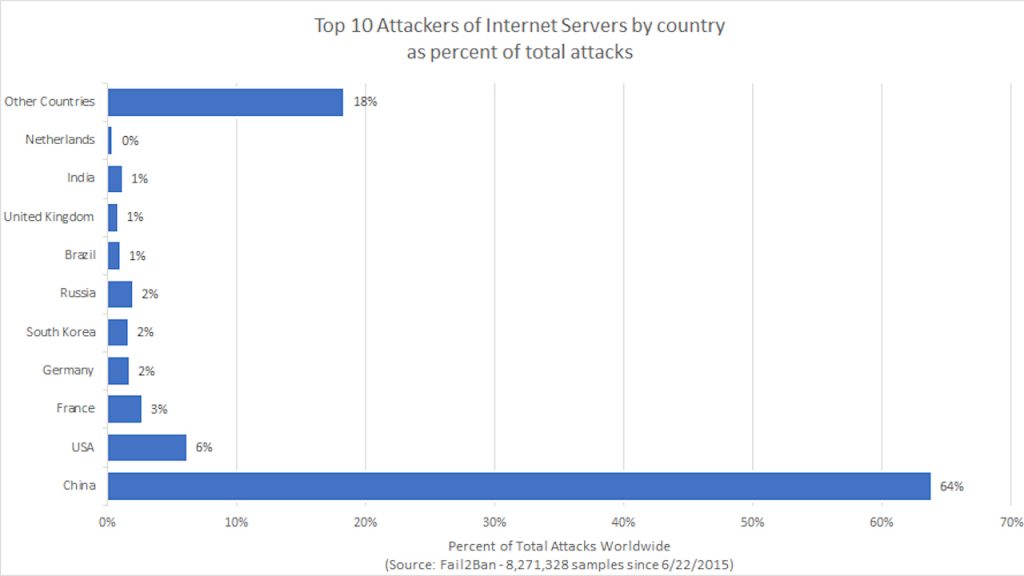
A recent report using fail2ban data, collected over 4 years since 2015, shows China as the source of 64% of cyber attacks on internet servers located around the world. These are break in attempts detected by the security monitor. The attacks from Russia, USA, and France pale in comparison.
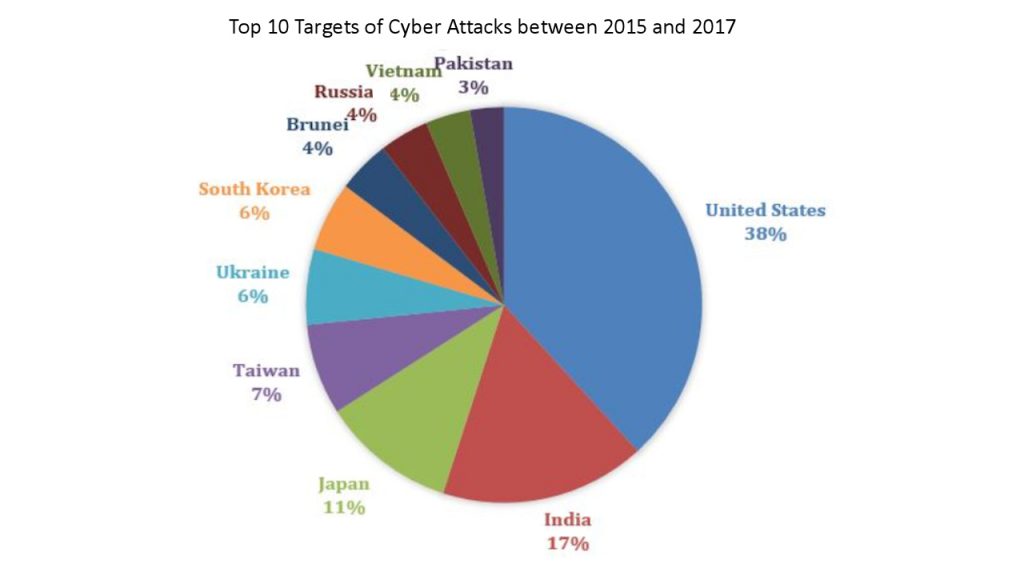
Symantec’s Norton Security suite reports, between 2015 and 2017, the United States was targeted for cyber attacks 38% of the time . 64% of attacks on US servers came from China.
Documents, designs, and plans obtained from successful break-ins to a server can then be transferred to a state owned and/or subsidized company for competitive manufacture, financial, military, or security purposes.
Forced Technology transfer can result in designs being transferred to a majority owned Chinese company. Such designs may be leaked to another entity which forms a company to compete with the original product. The new independent company has access to state subsidies which compensate for loss taking in order to capture a greater percentage of the market. Eventually the original joint venture may go out of business.
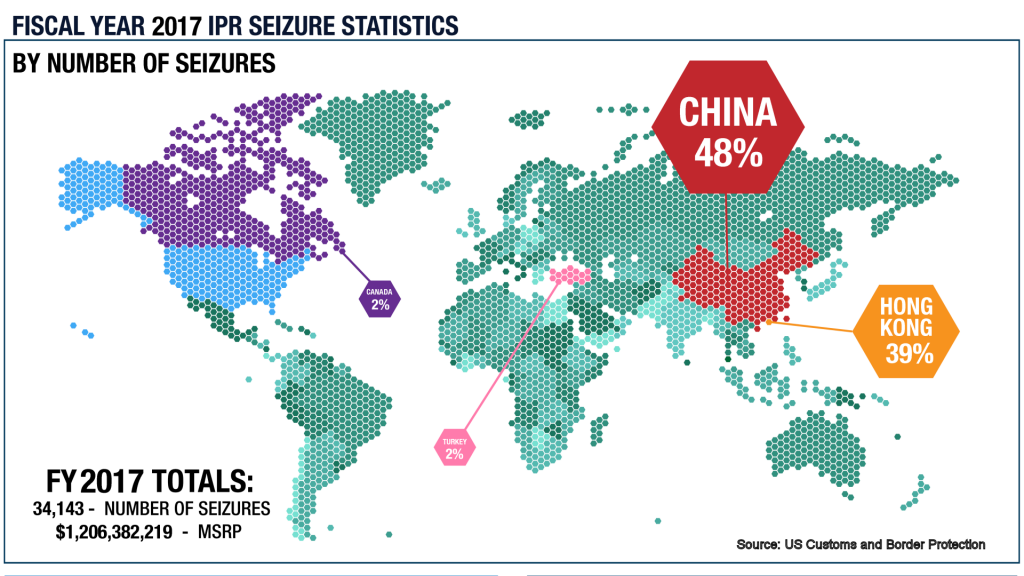
As counterfeit products stream into the USA, only a small percentage are physically checked. Of the items checked Intellectual Property theft seizures show. 48% from China and 39% from Hong Kong totaling to 87%.
Where does Hong Kong get its Products? From the Schenzhen zone across the river into mainland China. This place houses the headquarters of #Huawei and many other technology and industrial companies which manufacture to supply the export market.
Using the strategy of combining intellectual property theft with currency manipulation, state owned and subsidies companies, and product dumping China has contributed to the virtual gutting of the USA rust belt. This has led to some population flight to urban cities on both coasts. The US and other western nations have brought up these issues since the China entered the World Trade Organization in 2001.
It has been suggested publicly on multiple occasions in the intervening years that China does not play by the same rules. They have not complied and do not implement all WTO rules and standards. There is a lack of trust that intellectual property theft claims can be adjudicated in a Chinese court.
The American manufacturing capacity has suffered since NAFTA in 1992. As a result many cities especially in the Rust-belt have lost millions of jobs. The USA has spent 8 to 10 trillion US dollars pursuing wars in Afghanistan, Iraq, Syria, and other places in the middle east.
Adding the Chinese trade deficit to these other costs saps the wealth and the energy from the USA.
Companies that move their manufacturing to China and have listing on a US stock exchange argue for a deal which will somehow preserve the status quo. Good Quarterly Reports are all important lest stock prices fall.
The national security impact on the United States is very real. Reports claim that some Chinese electronic parts are used in the latest F-35 fighter aircraft. Other raw materials such as steel and aluminum may also be shunted into the supply chain for military equipment manufactured in the USA.
The latest threat of Huawei 5G networks opens US networks to greater cyber intrusions from China without much counter balance from US manufactured products. This technology may also be shifting surveillance capabilities from the NSA to Chinese intelligence services.
The opaque nature of hardware and software makes it difficult if not impossible to detect flaws or back doors that allow for data to be siphoned from a piece of equipment. Remote control tactics can mask a backdoor such that it is not detected during testing. Software updates can introduce malware and/or new back-doors.
At the end of the day a trade agreement with China has to be based on trust. This trust is unlikely to be developed in the near future. Its more likely China may become satisfied with the wealth and technology transfer that received thus far and strike an independent path. Its hard for 300 million Americans to carry 1400 million Chinese.
